What is a Context-Menu?
A context-menu is simply the menu that appears when you right-click an object in the File Explorer or Desktop. It allows applications to add functionality when interacting with files such as “Edit with Notepad++”.
How Can We Leverage This To Our Benefit?
After doing some research about DLL proxying I accidentally stumbled across a method of persistence that doesn’t seem to be documented anywhere. I was able to leverage the context-menu handler autorun feature of file explorer to gain persistent access to the system via a DLL which is loaded in explorer.exe.
Why Is This So Dangerous?
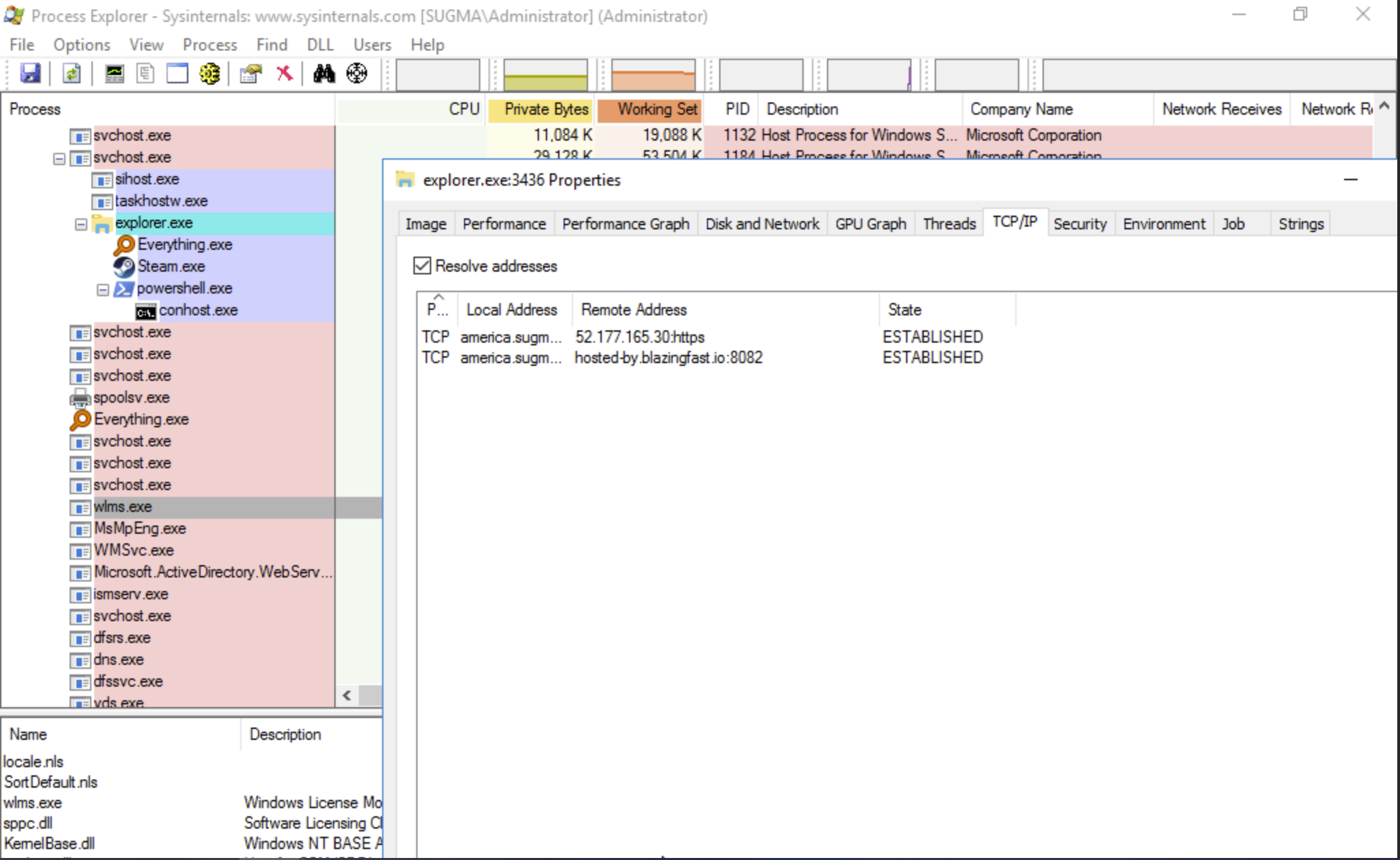
The main reason this is so dangerous is that the DLL is being run by explorer.exe, this is a trusted program, where network traffic normally comes out of for stuff such as SMB and HTTP requests(Windows telemetry). Also since its loaded via explorer.exe, it’s impossible to kill unless you kill each thread, otherwise, you will kill your user interface such as the taskbar, desktop, and file explorer. Also, it gets run every reboot ;). In the screenshot below using process explorer, you can see two connections, one is Blazing Fast(my backconnect), the other is a Windows telemetry server.
How Does DLL Hijacking Play Into This?
Essentially we can perform DLL hijacking to have a malicious DLL be called and redirect the normal execution of the legitimate DLL to the real library. DLL proxying is a form of DLL hijacking, where a malicious DLL also known as a wrapper redirects all function calls to the legitimate DLL. This is achieved by making a forwarder, which points to the legitimate DLL by supplying a string that contains the name of the function, the DLL it’s going to be redirected to, the name of the function in the real DLL and the ordinal which is the unique identifier for an exported function.
Steps to Develop Your Own persistence
Step 1, Finding a Suitable Program Which Has a Context Menu Handler
All right this should be common sense at this point, for this demonstration we will be using Notepad++, really any other text editor or program that gets called in the context menu can be used. In the screenshot below we’re using autoruns by Sysinternals, to see the programs which have a context-menu registry entry.
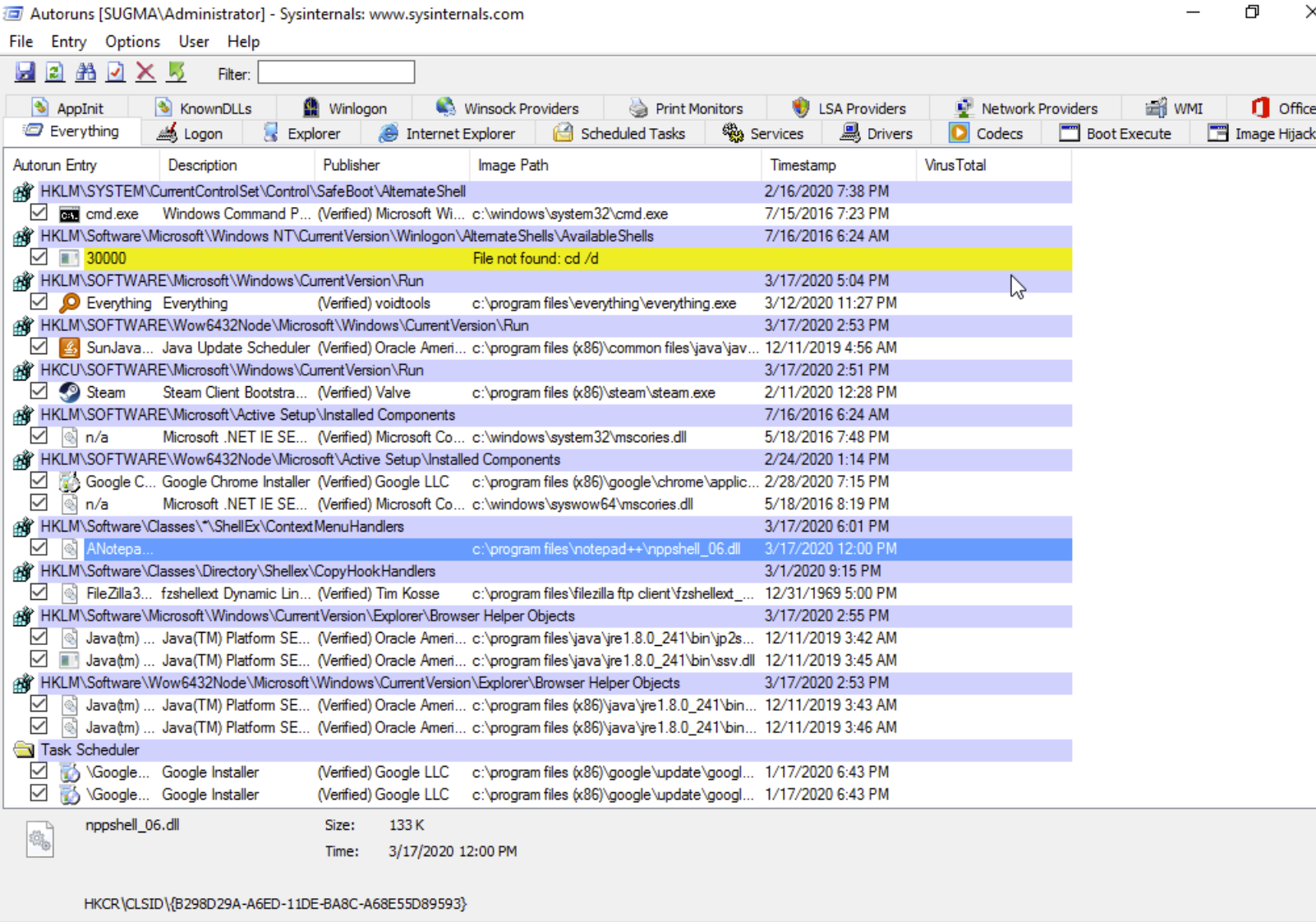
Step 2, Create a Proxy DLL
In our case we will replace the real DLL NppShell_06.dll with our malicious one and rename the real DLL to NppShell_06_.dll which will have the legitimate function calls proxied to it. Our payload will be ran in the BOOL WINAPI DllMain(...) function, and will create a thread to run parallel to the program which will not halt the flow of the DLL, note: if you keep a loop inside of the DLL main function it can cause programs to entirely halt as the LoadLibrary(...) function call waits for the loading of a specified DLL to end before continuing the normal execution of the program.
In my Github repository, https://github.com/rek7/dll-hijacking, I provide a basic script and a DLL that can be used. Continuing with our Notepad++ demonstration, I will use my tool parse.py to create a custom definitions.h file for NppShell_06.dll with the name of the functions we have to proxy.
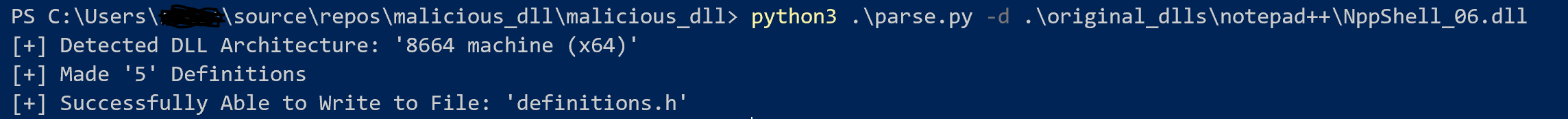 Your definitions.h should look like:
Your definitions.h should look like:
#pragma once
/*
.\original_dlls\notepad++\NppShell_06.dll - 8664 machine (x64)
*/
#pragma comment(linker,"/export:DllCanUnloadNow=NppShell_06_.DllCanUnloadNow,@1")
#pragma comment(linker,"/export:DllGetClassObject=NppShell_06_.DllGetClassObject,@2")
#pragma comment(linker,"/export:DllInstall=NppShell_06_.DllInstall,@3")
#pragma comment(linker,"/export:DllRegisterServer=NppShell_06_.DllRegisterServer,@4")
#pragma comment(linker,"/export:DllUnregisterServer=NppShell_06_.DllUnregisterServer,@5")At this point, you should be all set, compile your DLL to be the same as the identified one.
Step 3, Deployment
In our case, rename the original NppShell_06 DLL to NppShell_06_.dll and place our new DLL as NppShell_06.dll. Simply restarting the computer should load our DLL into memory, and run our payload.
Example of Shell Being Spawned
In the screenshot below, the DLL is triggered when the user right-clicks which activates the context menu since DLLs are loaded into memory only once as soon as it’s activated it will continue to be in memory until the system restarts.
Methods of Detection
At this point, it’s completely FuD by all major anti-viruses and Palto Alto Wildfire. One of the easiest ways to detect it is to check for unsigned DLLs that are being loaded.